Forrester’s State Of Application Security Report, 2021: Key Takeaways

Forrester’s Annual State of Application Security Report has become a touchstone for organizations on their journey to achieve AppSec maturity. As the software development industry and threat landscape continue to evolve, Forrester’s State of Application Security Report for 2021’s main message is that while applications are still a major attack vector, analysts found signs of hope in their research.
We’ve put together the main takeaways from Forrester’s report for 2021, covering why applications remain a top attack vector, application security trends, and which tools and processes organizations should put into place to achieve an effective application security strategy.
Applications are Still a Top Attack Vector
While reliance on applications has grown steadily over the past few years, the report explains the shift to remote work drove companies to rely on applications even more, which explains why the research shows that web applications are the most common form of external attack, followed by software vulnerabilities.
The report predicts that web applications will continue to be a main vector for external attacks, listing three main reasons:
- The continuous growth in open source usage
- A substantial increase in security research, resulting in a rise in the number of reported security issues including a high number of API vulnerabilities
- the growing popularity of containerized environments, which suffer from a high volume of code and configuration issues
According to the report, many organizations plan to prioritize improving their AppSec profile in the upcoming year, and 21% of security decision-makers surveyed said their companies will prioritize building security into development processes.
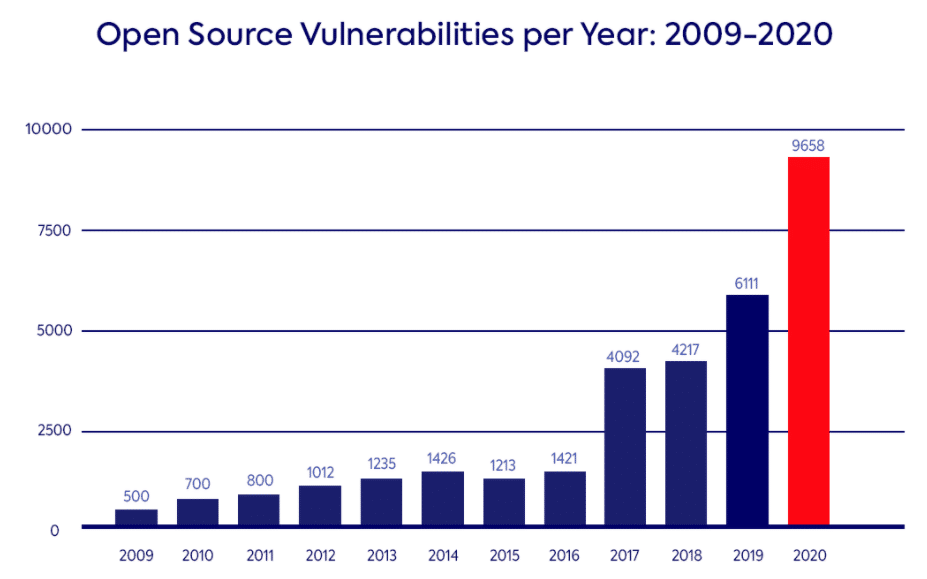
Data from: Mend Annual Report, Open Source Vulnerabilities 2021
AppSec Tooling Helps Bridge the Gap Between Security and Developers
The report provides a number of recommendations that can help organizations bake security into the software development life cycle (SDLC). The first is to integrate automated application security testing into the DevOps pipeline – a practice that is now relatively easy to adopt with “prerelease testing products offering deep integrations with core development tools like Azure DevOps, GitHub, Jenkins, and Jira.”
While automating application security testing early in development as part of the DevOps pipeline is important, the report recommends finding ways to speed up remediation once security issues are detected. It’s important to combine the vulnerability scan results to both improve visibility and get vulnerability prioritization right so that the most urgent issues are remediated swiftly.
Shift-Left Continues, but Adoption of New AppSec Tools Is Inconsistent
The report points to some encouraging trends when it comes to the integration of automated security testing tools into the DevOps pipeline and advises that “new development approaches call for new tooling, and firms must keep up with the evolving protections to protect emerging application architectures.”
One of the Forrester report’s top recommendations for updating and improving AppSec tools and processes is shifting security testing left. According to Forrester data, security pros continue to invest in shifting security left, implementing testing tools early in the development process, understanding that this shift enables quicker remediation.
The report also presents an increased focus on API security, while container security lags behind, despite the growing popularity of containerized environments.
AppSec Strategies Should Keep Up with Agile Development Processes
Forrester’s State of Application Security for 2021 highlights the fact that organizations are increasingly relying on open source and third-party components, opening up more APIs externally. The report urges security pros to nurture communication between security and development teams and to embrace automated security testing tools throughout development.
Forrester emphasizes the importance of creating tools that developers love. As advanced AppSec tools focus on developers, it’s important security professionals collaborate with development teams to ensure security is woven into development workflows.
In addition to using tools that easily integrate into development environments, it’s also important to provide developers with remediation guidance, and automate work processes like sign offs for policy creation and exceptions. Another crucial point is that application security tools should not stop at detection, rather provide automated support for prioritization of security issues.
The report states that as the software development ecosystem evolves “new development methodologies mean changes to the traditional security paradigms.” This calls for investing in updated application security tools that can be easily integrated in future application development plans and architecture.
The report also recommends investing in and cultivating developer security champion programs in order to promote a shared sense of ownership over security tasks. This will help organizations ensure that the shift left approach is being implemented and that security is addressed early in the development process.
Focusing on the Wide Open Source Threat Landscape
The Forrester report addresses the emergence of supply chain attacks, which have recently featured heavily in the news. The report reminds readers that it’s important to focus on the wider open source threat landscape.
While it’s important to pay attention to security risks to the supply chain, the report urges organizations to remain aware of open source security risks. It’s as important as ever to continuously detect and remediate vulnerabilities in open source libraries in order to ensure security and keep products and customers safe.
