
Cybercrime has grown exponentially in recent years. With millions of mobile devices and laptops being sold worldwide, malicious attackers are getting more and more opportunities to illegally harvest private user information and data. Companies and organizations are beginning to take a proactive approach to safeguard their applications and mitigate vulnerabilities before they are maliciously exploited.
Numerous security solutions are being implemented to combat these cyber threats, yielding varying levels of success. While Dynamic Application Security Testing (DAST) and Penetration (Pen) Testing provide good post-development coverage, there is a growing demand to detect vulnerabilities early in the Software Life Cycle (SLC).
Static Application Security Testing (SAST) is arguably best suited to address the aforementioned security need. One such SAST solution is Source Code Analysis (SCA), which involves the scanning of source code. This article will help shed some light on why SCA is proving to be an effective and cost-efficient way to secure applications.
Insecure application coding and its implications
As mentioned earlier, web and mobile applications are being raided by malicious attackers who exploit a wide range of vulnerabilities. The most common ones include SQL injections, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) and Directory Traversals, regular starrers in the widely recognized OWASP Top-10.
According to a study conducted by Ponemon Institute, not having a secure development process can prove to be very expensive. Vulnerabilities detected in the production stage cost around $7600 on average to fix, but the financial damage caused is significantly lower when detected early on in the process (only $80 per defect on average).
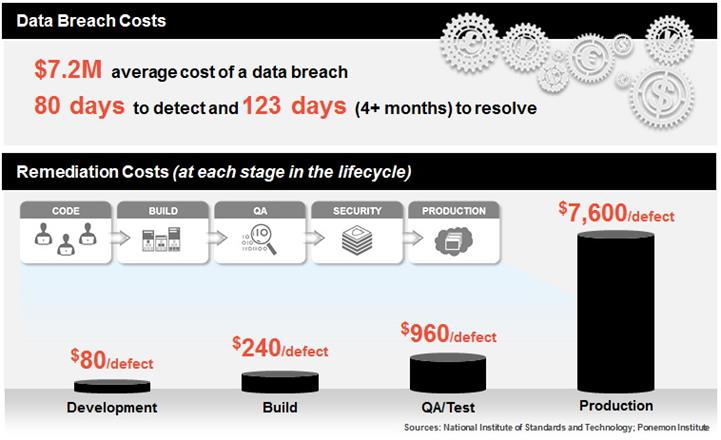
Besides the monetary implications, companies and organizations have to deal with other serious issues once their application has been breached. These include brand image restoration, damage control expenses, customer retention efforts and other technical problems that arise with the exploitation of application layer vulnerabilities.
What is Source Code Analysis (SCA) and how does it help?
In a nutshell, SCA is a SAST solution that enables the creation of a secure Software Development Life Cycle (sSDLC). This means that the security process starts from the very beginning, enabling the detection of vulnerabilities even before the code reaches the build stage of the development process. Benefits of implementing SCA include:
- Full control over the SDLC security standards.
SCA can be seamlessly integrated into the various stages of the SDLC such as source repositories, build management servers and bug tracking tools. This gives the auditors the option of treating security requirements as checkpoints and halting the build as soon as vulnerabilities are detected. - Effective integration into the developer environment.
Many SCA solutions offer IDE plugins (Eclipse, IntelliJ, Visual Studio, etc) that makes life easier for the developers, helping them code more securely. No heavy third-party software installations are required and maintenance is virtually a non-issue. Some SCA companies even offer the option of directly uploading projects for scanning. - Support for Agile and DevOps.
More and more software companies are gravitating towards Agile and DevOps. Implementing SCA solutions in these scenarios allows technology leaders to act as security champions. Security also becomes an integral part of scrum meetings and the developers know exactly what’s needed of them.
Another added benefit of implementing SCA is the systematic improvement made in code standards. Companies have the ability to scrutinize the integrity of the application code and locate errors such as memory leaks, logic issues and anti-patterns. Once these are detected, developers eventually learn to churn out code with minimal flaws.
A 2014 McAfee report brought up some statistics that highlight the importance of application security. For example, the global “internet economy” generates between 2 to 3 trillion dollars annually, with cybercrime claiming almost 20% of the value created. This harmful trend has to be brought under control sooner than later.
With cybercrime rising exponentially in recent years, application security can no longer be treated as an afterthought. CISOs and security officers can find the answer to most of their glaring security requirements by adopting static code analysis solutions. If the budget permits, SAST can ideally be complimented with DAST or Pen Testing.