SAST vs. SCA: 7 Key Differences

Everybody’s talking about securing the DevOps pipeline and shifting security left.. AppSec tools like SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing), and others that address issues in proprietary software have become staples of the developer’s security toolbox. In addition, an AppSec strategy also needs to detect open source components with known vulnerabilities, and that’s where SCA (Software Composition Analysis) tools play an important role. Both SAST and SCA tools address vulnerabilities management. Each one operates differently, covers a different set of vulnerabilities, and even integrates into different stages of the software development lifecycle (SDLC).
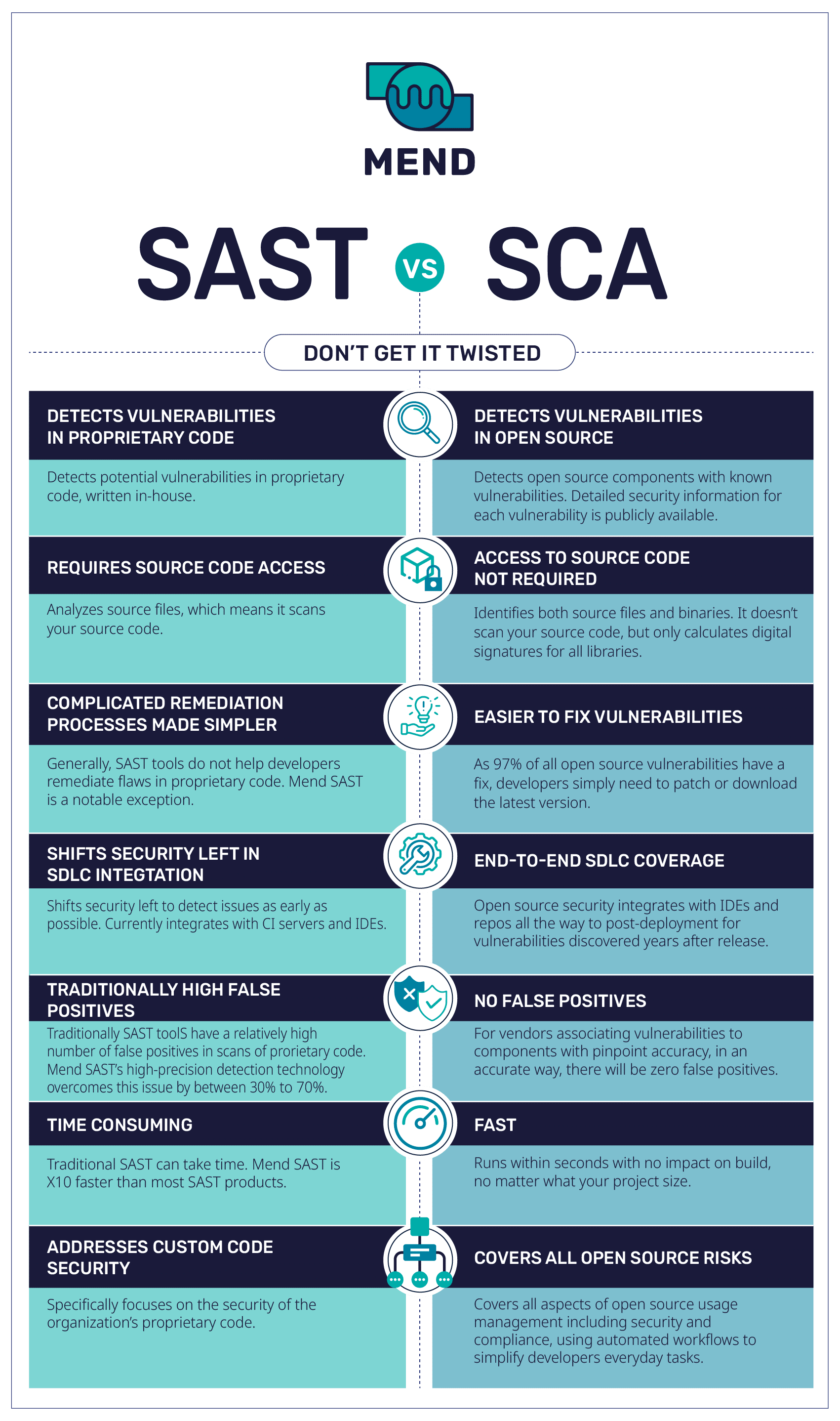
There are quite a few differences between SAST and SCA tools. SAST tools detect security vulnerabilities in proprietary code by scanning the code while it’s still in a static/non-running state. This helps developers remediate issues in their code before it’s deployed.
SCA tools detect and track all open source components in an organization’s codebase, to help developers manage their open source components. Advanced SCA tools automate the entire process of managing open source components, including selection, alerting on any security or compliance issues, or even blocking them from the code. They also provide comprehensive information about the open source vulnerabilities discovered so that developers can easily fix them. SCA tools can be used throughout the SDLC, from creation to post-production.
7 Key Differences Between SAST and SCA
#1 Vulnerabilities Detection
SAST tools scan an organization’s in-house-written code for potential vulnerabilities, based on a set of predetermined rules. SCA tools track an organization’s open source components and identify whether any contain known vulnerabilities. When vulnerabilities are discovered, SCA tools provide detailed information about the vulnerabilities to help developers remediate them swiftly.
#2 Requires Source Code Access
SAST tools focus specifically on analyzing source files. That means that they scan a product’s source code. In contrast, an SCA tool discovers all software components including their supporting libraries as well as all direct and indirect dependencies. This can be done without giving the SCA tool access to the source code.
#3 Remediation
Generally speaking, SAST tools do not help the developer remediate flaws in proprietary code. This is because proprietary code tends to be unpredictable. It doesn’t fit neatly into known patterns, so it is hard for a SAST tool to suggest how to remediate the flaw. (Mend SAST is a notable exception.) In contrast, SCA tools typically provide some kind of remediation advice because the remediation is usually quite predictable and straightforward: “Replace library 1.0.1 with library 1.0.2.” Open source vulnerabilities are easy to fix since 97% of all open source vulnerabilities have a fix validated by the open source community and developers simply need to patch or download the latest version.
#4 SDLC Integration
SAST and SCA tools can both be integrated early in the development process to help developers catch vulnerabilities as early as possible before they become more expensive and time-consuming to fix. Both SAST and SCA tools integrate with CI servers and IDEs. SCA tools offer end-to-end SDLC coverage all the way to post-deployment — providing coverage for vulnerabilities discovered years after release.
#5 False Positives
Traditional SAST tools often produce a relatively high number of false positives. (Here again, Mend SAST is a notable exception.) SCA tools, by contrast, are not looking to detect new vulnerabilities but to identify the open source components that have known vulnerabilities associated with them. Since the task here is to accurately identify vulnerable open source components, with the right SCA tool, it is much easier to have zero false positives.
#6 Timeframe
Running source code scans with traditional SAST tools is often a time-consuming task, sometimes lasting many hours. In contrast, SCA tools typically run within seconds, no matter how large the project is. Mend’s SAST technology speeds up the scanning process. It’s 10 times faster than most SAST products, offering the fastest scanning capability of its kind.
# 7 Risk Coverage
SAST tools can identify a wide range of potential code flaws, commonly known as CWEs. The most common CWEs are described in lists such as the OWASP Top 10 and the MITRE Top 25. All of these code flaws are security risks. In contrast, SCA tools identify both security risks and license compliance risks that are associated with open source software.
SAST vs. SCA: The Secret to Covering All of Your Bases
As you can see, comparing SAST to SCA is like comparing apples to oranges. Both of these tools help developers ensure that their code is secure. However, each one addresses different kinds of issues and goes about it in a very different way. Each tool deals with a different set of issues, using a different technology. Our best advice is to work with a vendor that understands the differences and offers a solution for both.
