How To Secure Your SDLC The Right Way

The ever-evolving threat landscape in our software development ecosystem demands that we put some thought into the security controls that we use throughout development and delivery in order to keep the bad guys away. This is where the secure software development life cycle (SSDLC) comes into play. Organizations need to make sure that beyond providing their customers with innovative products ahead of the competition, their security is on point every step of the way throughout the SDLC.
In order to achieve a secure SDLC, we need to make sure that we are taking a number of important yet often overlooked measures and using the right tools for the job along the way.
What is a secure SDLC?
In a secure SDLC, security is integrated throughout the development and delivery cycle and implemented in every stage. The SSDLC is designed so that security issues are detected and remediated as early as possible, rather than relegating security testing to the later stages of development when issues are significantly more expensive and time-consuming to address.
Achieving an SSDLC requires organizations to adopt an updated set of security practices and processes, and a DevSecOps approach. This new approach addresses every aspect of the SSDLC to ensure security is baked into the entire development process and to speed up detection and remediation. This includes updating processes so that security is tested early and often, integrating automated application security testing tools throughout the SDLC and ensuring that security, DevOps, and development teams are working together toward the shared goal of secure development and delivery.
According to Forrester’s recent State of Application Security Report, security pros in software development organizations have already started investing in achieving a SSDLC and are implementing testing tools early in the development process.
Why it’s important to secure the SDLC
Over the past years, attacks on the application layer have become more and more common. Ponemon’s recent research report on reducing enterprise AppSec risks found that the highest level of security risk is considered by many to be in the application layer.
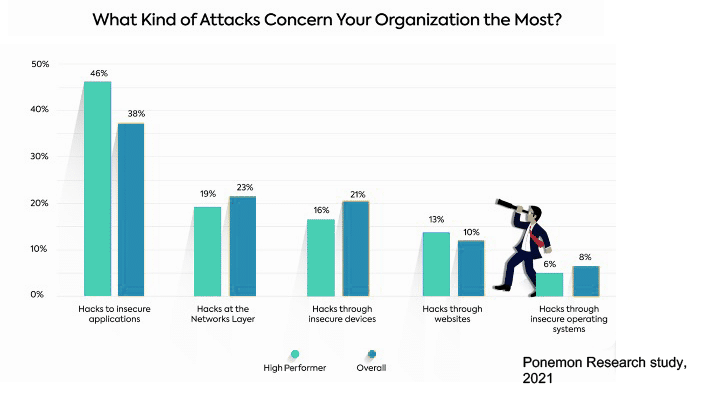
The research surveyed over 600 IT and IT security practitioners to examine the reasons why enterprises’ concern over application security continues to rise. The report presents some interesting results. Respondents’ reported an inability to quickly detect vulnerabilities and threats, in addition to an inability to perform quick patching in production. Nearly 60% said it can take days, weeks, and even months to patch in the production phase.
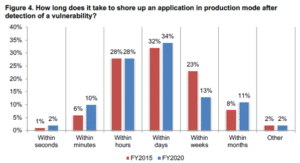
When an SSDLC is put into place, these issues can easily be addressed.
How can we achieve a secure SDLC?
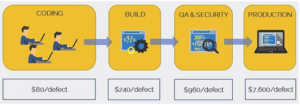
Shifting security left is an important principle in the SSDLC. This requires development and security teams to incorporate updated security practices and tools throughout the software development lifecycle, starting from the earliest phases. Shift left security helps organizations save a lot of time and money later on since the cost of remediating a security vulnerability in post-production is so much higher compared to addressing it in the earlier stages of the SDLC.
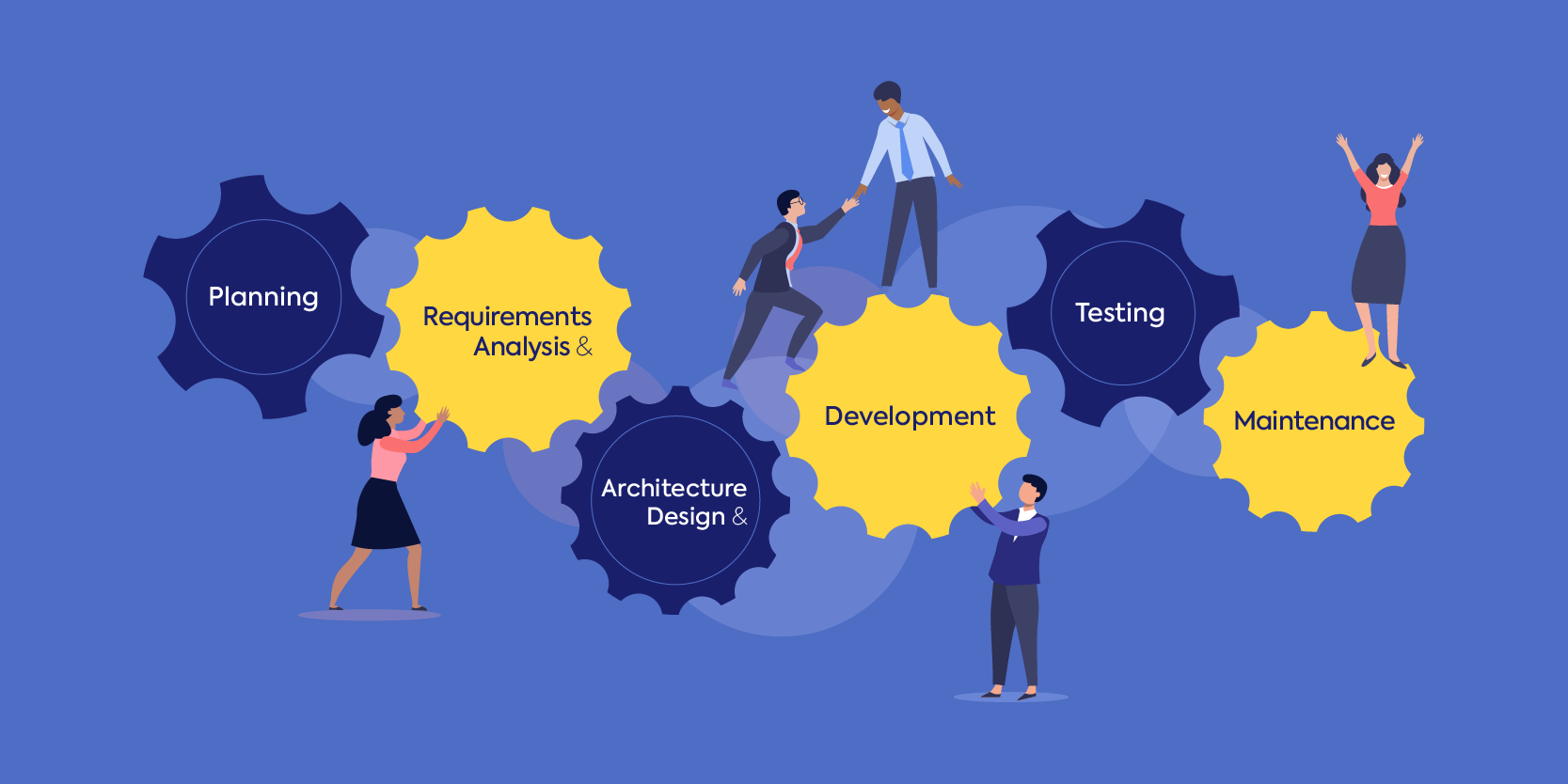
Embedding security into all phases of the SDLC
Each step in the SDLC requires its own security enforcement and tools. Throughout all phases, automated detection, prioritization, and remediation tools can be integrated with your team’s IDEs, code repositories, build servers, and bug tracking tools to address potential risks as soon as they arise.
#1 Planning
In the first planning phase, developers and security experts need to think about which common risks might require attention during development and prepare for it.
#2 Requirements and Analysis
In the second phase of the SDLC, decisions are made regarding the technology, frameworks, and languages that will be used. This is when experts should consider which vulnerabilities might threaten the security of the chosen development tools in order to make the appropriate security choices throughout design and development.
#3 Architecture and Design
In this phase, teams should follow the architecture and design guidelines to address the risks that were already considered and analyzed during the previous stages. When vulnerabilities are addressed early in the design phase, you can successfully ensure they won’t damage your software in the development stage. Processes like threat modeling and architecture risk analysis will make your development process that much simpler and more secure.
#4 Development
During the development phase, teams need to make sure they use secure coding standards. While performing the usual code review to ensure the project has the specified features and functions, developers also need to pay attention to any security vulnerabilities in the code.
#5 Testing
The testing phase should include security testing, using automated DevSecOps tools to improve application security.
It’s important to remember that the DeSecvOps approach calls for continuous testing throughout the SDLC. Testing early and often is the best way to make sure that your products and SDLC are secure from the get-go. That means teams should start testing in the earliest stages of development, and also that security testing doesn’t stop at the deployment and implementation stage.
#6 Maintenance
While your teams might have been extremely thorough during testing, real life is never the same as the testing environment. Be prepared to address previously undetected errors or risks and ensure that configuration is performed properly.
Even after deployment and implementation, security practices need to be followed throughout software maintenance. Products need to be continuously updated to ensure it is secure from new vulnerabilities and compatible with any new tools you may decide to adopt.
Keeping an eye on open source security
Another risk that needs to be addressed to ensure a secure SDLC is that of open source components with known vulnerabilities. Since today’s software products contain between 60%-80% open source code, it’s important to pay attention to open source security management throughout the SDLC. Software Composition Analysis (SCA) tools are automated technologies that are dedicated specifically to tracking open source usage. They alert developers in real-time to any open source risks that arise in their code and even provide actionable prioritization and remediation insights as well as automated fixes.
Shift left to ensure a secure SDLC
The DevSecOps approach is all about teams putting the right security practices and tools in place from the earliest stages of the DevOps pipeline and embedding them throughout all phases of the software development life cycle. Securing your SDLC helps you to provide your customers with secure products and services while keeping up with aggressive deadlines.
As attacks are increasingly directed to the application layer and the call for more secure apps for customers strengthens, an SSDLC has become a top priority. It’s up to us to make sure that we’ve got full visibility and control throughout the entire process.
