Hitting Snooze on Alert Fatigue in Application Security


Medical devices, subway car doors, severe weather warnings, heavy machinery, car alarms, software security alerts. They all notify you to indicate that something is wrong so that you can take action to prevent harm. Hospital monitors can detect a wide range of issues, from an incorrect dose of medication to an irregular heartbeat and beyond. They can quite literally save a life. The same goes for severe weather alerts that warn of impending tornadoes or hurricanes. Though life doesn’t hang in the balance with software security alerts, they can illuminate risk vectors that might otherwise go unnoticed and could potentially have a big impact on your organization should a breach occur. The commonality among these alerts is that they are designed to automate a process to help us not hurt us.
The promise of automation is to make our lives better, safer, easier, which is why these automated alerts were designed in the first place. So what happens when these alarms ring so frequently – or there are so many of them – that they become background noise? What if more than half of these alerts are false alarms? Suddenly a hospital monitor put in place to detect signs of sepsis is silenced or ignored, putting a patient at risk. Or the volume of application security alerts is so great that it is near impossible to address each and every one of them before an application is put into production. The end result of ignoring these alerts is increased risk of harm. It’s no wonder that many industries have identified alert fatigue as a serious problem.
What Exactly Is Alert Fatigue?
Alert fatigue, also called alarm fatigue, is when an overwhelming number of alerts desensitizes those professionals responsible for monitoring them. This desensitization leads to either missed or ignored alerts and results in a delayed response or no response at all.
Prevalent across a wide range of industries, alert fatigue negates the original purpose of automated alerting systems: to identify and resolve potential problems before they become catastrophic. Managing and remediating these alerts is an essential component in preventing this critical issue.
How Does Alert Fatigue Apply to Application Security?
In application security, alert fatigue refers to the overwhelming number of security alerts that developers and security professionals receive on a daily basis. These alerts may be generated at any point in the software development life cycle (SDLC) from a scan of an application’s codebase pre-build, during QA, or in production. High rates of false-positive alerts cause excessive noise and compound the problem. Too many alerts and false alarms make it extremely difficult to pinpoint the critical vulnerabilities that have the potential to cause the most harm.
Security alerts have more than doubled over the past five years. Prioritizing and remediating these high alert volumes is a significant challenge. It’s no surprise that the vast majority of security teams identify alert fatigue as a serious problem, adding to organizations’ security debt, which is the backlog of security vulnerabilities that have not been addressed and that leave organizations open to malicious attacks.
The Problem with Detection
For so long application security testing focused on detection. It was the logical place to start. After all, you can’t fix a problem if you don’t know it exists. Unfortunately, detection isn’t the be-all and end-all for managing security vulnerabilities. First, high rates of false positives in early stage detection generate a lot of noise, adding to the problem of alert fatigue. Second, detection only identifies problems; it provides no actionable data on how to rectify issues. Without advice on how to resolve security vulnerabilities, alerts continue to pile up, exacerbating alert fatigue.
As application security technology matures, the issue of false positives will naturally be resolved. And in fact this has already happened with technologies that guarantee no false positive alerts. Even with solutions that promise zero false positives, however, detection still isn’t enough on its own. Security professionals are dealing with an enormous volume of alerts daily, and it is impossible to fix every alert. Furthermore, not every alert is created equal. Not every alert is of the highest priority representing a critical vulnerability.
Prioritization and Remediation
If detection on its own is part of the problem, the next logical step in dealing with the high volume of alerts in application security, then, lies in the prioritization and remediation of these alerts. Only by addressing these alerts do they go away.
Security professionals need to find a way to prioritize security vulnerabilities by determining which vulnerabilities pose the greatest risk or have the biggest impact then focus on fixing those first. The challenge here is that no gold standard currently exists for vulnerability prioritization. Should organizations focus on vulnerabilities that are the easiest to fix? The most prevalent? Those that have the biggest impact on your business? Each organization prioritizes alerts differently, and even different teams within the same organization take divergent paths to prioritization.
Once you have prioritized alerts to address those you have identified as most critical, you need to begin the work of remediating these security vulnerabilities. Remediation is the ultimate goal for any security vulnerability, however, the path to a fix is not always obvious. To address this, you need a solution that identifies both how to remediate a vulnerability, but also how likely that vulnerability can be updated without breaking your application.
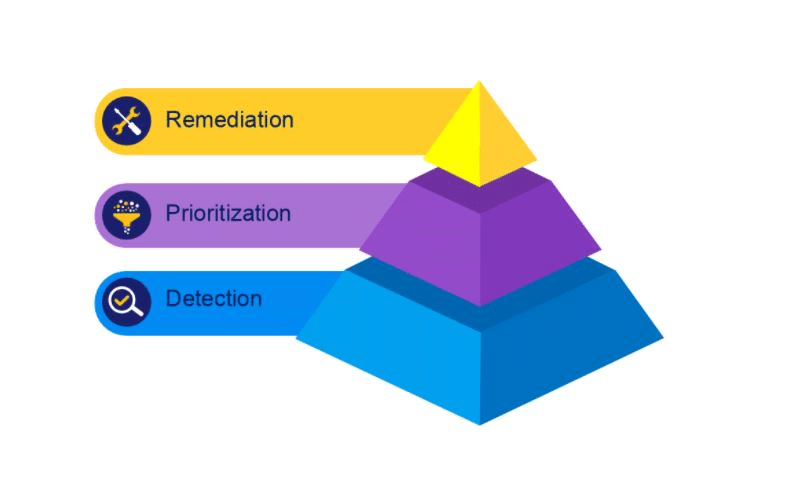
The best approach to application security is one that has matured beyond simple detection to focus on the higher order functions of prioritization and remediation. Once you begin to remediate vulnerabilities using automation, alert fatigue will start to subside.
What Can You Do to Prevent Alert Fatigue?
To address the problem of alert fatigue, take these practical first steps:
-
Tune your system to reduce the amount of background noise. Look for security solutions that offer zero false positives and give you contextual data so that you understand the severity and relevance of alerts.
-
Implement solutions that prioritize your security vulnerabilities, so you can concentrate first on the high-severity issues that have the potential to cause the greatest disruption.
-
Automate as much of this process as possible so that your security professionals are free to remediate the most important threats first.
Don’t Hit Snooze on Security Alerts
Although alert fatigue is a problem in application security, you can’t just hit snooze and expect it to go away. Even though we have reached a point where organizations are no longer able to address all vulnerabilities because of the sheer numbers, you can manage alert fatigue so that it’s not running your life and increasing your risk. Technologies are available to filter out the noise and help you prioritize and remediate your security vulnerabilities so that you aren’t falling asleep on the job.
