March Open Source Security Vulnerabilities Snapshot


We are already deep into Q1 2020, and we thought it would be a good time to take a look at some of the data we’ve already gathered this year to learn about the new open source security vulnerabilities published in February, what we should look out for, and how the community is addressing the newest challenges.
Our research team took a deep dive into the Mend database to learn about the new open source security vulnerabilities published in February so that we could provide you with an updated overview of the latest open source security vulnerabilities out there. The Mend vulnerability database continuously aggregates data about open source vulnerabilities from multiple sources including the National Vulnerability Database (NVD), and additional publicly available, peer-reviewed security advisories and issue trackers in the open source and security communities.
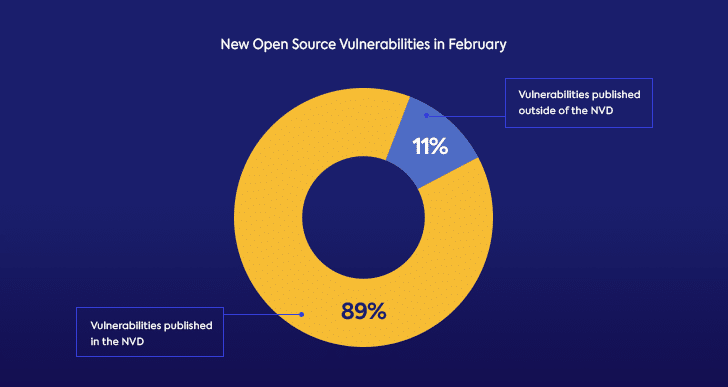
February saw nearly 650 new open source security vulnerabilities published. Over 10% of them were published on community resources outside of the NVD, on various open source community forums, advisories, and issue-trackers. Considering the decentralized nature of the open source community, these figures should come as no surprise. While the NVD database is often the go-to for security experts and developers looking for information about security vulnerabilities, it doesn’t include all of the security vulnerabilities published. Many issues that are reported in various public open source resources aren’t immediately added to the CVE, and can often be added to weeks, months or even years since their initial publication. That’s why when addressing open source security, it’s important to cover multiple community resources, and not rely solely on the NVD.
Open Source Vulnerabilities Severity Breakdown in February
Beyond the overall number of newly published open source security vulnerabilities in February, we also wanted to look at their severity scores.
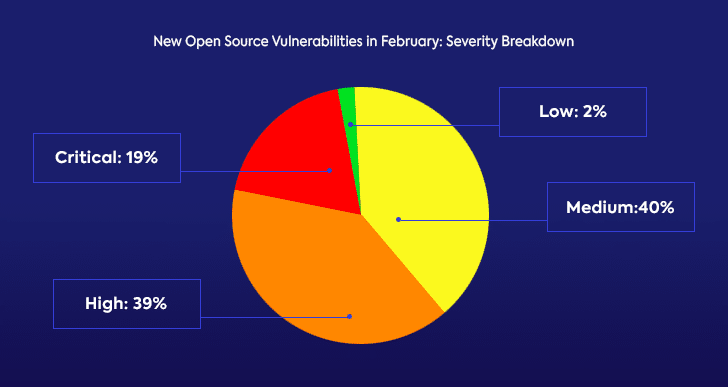
Looking at the severity distribution of the CVSS v3 scores for new open source security vulnerabilities in February, we found that 58% were either critical or high-severity. With the increasingly rising number of security alerts that development teams are required to address, this distribution is particularly concerning. Teams often look to severity scores to prioritize which issues to address first, and if nearly 60% of all open source security vulnerabilities are scored high and critical, addressing them all is a challenge.
It’s important to remember that while a vulnerability’s severity score should certainly be taken into consideration, there are additional factors that weigh in when attempting to figure out which security vulnerabilities require our immediate attention. Prioritization of open source security vulnerabilities should also include how much actual risk a vulnerability poses to your systems and projects, and how a vulnerable open source component impacts your code.
Top Open Source CWE’s in February
Another aspect that we wanted to take a closer look at in order to better understand which strategies to adopt when addressing open source security is the types of open source vulnerabilities published this month.
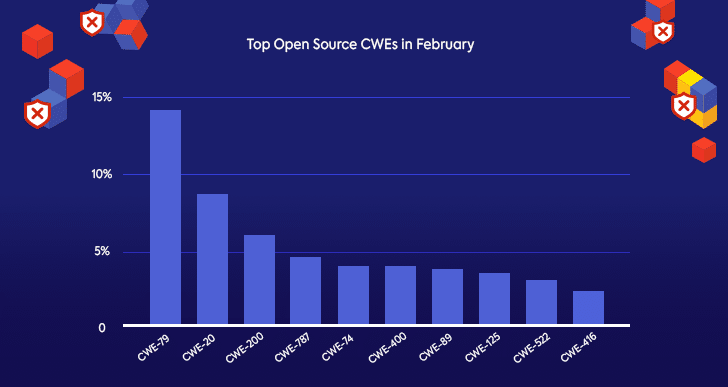
The top CWE this month is CWE-79, otherwise known as XSS (cross-site scripting). An XSS vulnerability occurs when an attacker is able to inject malicious script into a web page. This type of attack allows a hacker to access a wide variety of user information, like session tokens, cookies, and potentially any other type of information that the user provided to a presumably trustworthy website.
Number five in February’s top open source CWE’s list is CWE-74, which is the “parent” of CWE-79 (XSS), and therefore more abstracted. CWE-74 describes a general Injection weakness, not necessarily a script, and not necessarily related to a web page or site. CWE-74 occurs as a result of lack of input sanitation of a special element, like a comment section in a blog post, a URL, user authentication, or files parser. This CWE-74 can only be associated with a vulnerability if the vulnerability can’t be linked to one of its many children, for example, XSS, SQL Injection, Command Injection, Code Injection, and others.
Programming Languages and New Open Source Vulnerabilities in February
Since open source security starts with secure coding, we also wanted to check which programming languages saw the most open source vulnerabilities published in February.
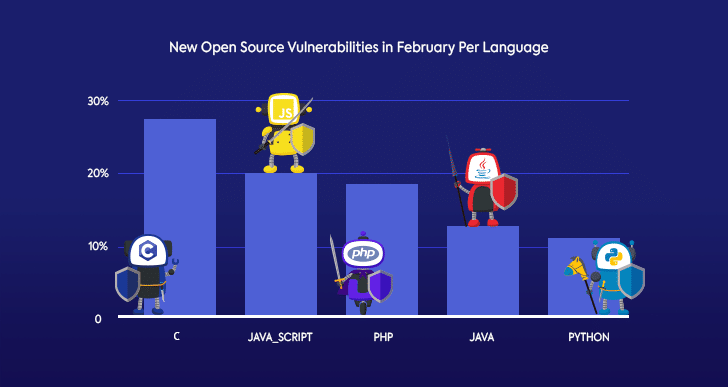
Understandably, some of the most popular programming languages saw the most new open source vulnerabilities. Since C has been around the longest, and probably has the most lines of code behind it, the language behind the Linux kernel came in first.
Not far behind is JavaScript, also a highly popular language. This also matches the top CWE’s data that we found, since XSS and injection issues are extremely common in JavaScript.
Spotlight on JavaScript XSS Open Source Vulnerabilities Published in February
Since XSS came in first in the common CWEs list, let’s take a closer look at two new open source security vulnerabilities published in February, which demonstrate CWE-79 and its parent, CWE-74.
CVE-2019-10785 is an XSS (CWE-79) vulnerability in the dojox project, originally a development area for the Dojo Toolkit, which contains packages that run the gamut of JavaScript technology.
Due to insufficient sanitation of their XML encoder, this vulnerability could allow attackers to inject a malicious XML file into the dojox xmpp server. On top of that, any user implementing “dojox.smpp.util.xmlEncode()” directly is vulnerable to this exploit. You can learn more about this issue and its fix on GitHub’s security advisory.
CVE-2019-10795 is a Prototype Pollution vulnerability in the undefsafe project. This issue occurs when insufficient neutralization of a user’s input (CWE-74) overwrites a JavaScript application object prototype, which eventually allows attackers to inject malicious code. Read more about this issue on GitHub.
Keeping Up with Open Source Security
There you have it folks, a snapshot of what’s happening right now in the fast-paced open source security space. One of the biggest take-aways from the data on new open source vulnerabilities in February is that the state of open source security is constantly evolving.
In order to keep up with the new open source security vulnerabilities published every month, it’s important that development, security, and DevOps teams continuously track the open source components that they are using throughout the development lifecycle, and keep up with any security updates from the open source community.
As the pace of development becomes increasingly rapid, it’s important that we keep up with the increasing number of open source vulnerabilities by integrating open source security tools and processes throughout our development lifecycle, to make sure that we address open source security vulnerabilities without letting them slow us down.
Want to learn more about February’s top open source security vulnerabilities? Check out Mend’s Vulnerability Database.
