Be Wise — Prioritize: Software Security Vulnerability Prioritization

As the number of known vulnerabilities continues to grow every year, software development and application security teams are increasingly relying on vulnerability detection tools throughout development. The result: teams are often overwhelmed with a steady stream of security alerts that must be addressed, and it’s becoming clear that it’s impossible to attempt to fix everything.
Once vulnerabilities are detected, teams need to find a way to prioritize them. The burning question that arises then is: what needs to be fixed first? How can software development organizations determine which security vulnerabilities pose the greatest risk, which ones demand their most immediate attention? How can development and security teams make sure they are not wasting valuable time fixing security issues that are not their biggest threat?
Vulnerability Prioritization Methods: To Each Their Own?
We asked our customers how they prioritize and found that the most common aspects that they consider when trying to determine the risk of a security vulnerability are those that are most easily available: vulnerability severity score (CVSS), ease of remediation, the vulnerability’s publication date, the popularity of the vulnerable software project, and the application type where the vulnerability was discovered.
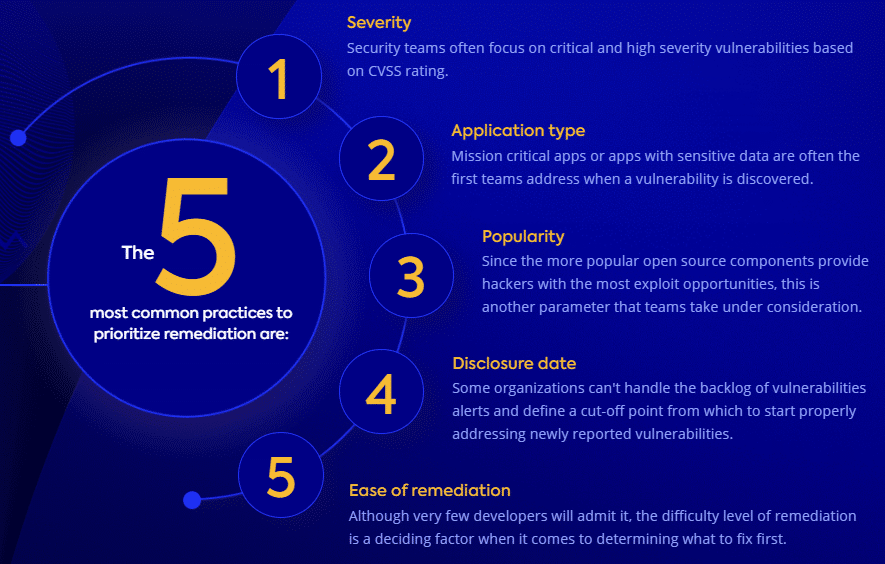
While each one of these prioritization methods have their merits, they are still far from perfect:
#1 Severity
Many application security professionals rely on CVSS ratings to determine which issues they need to fix first, and attend to critical and high severity issues. However, relying solely on this parameter is problematic for a number of reasons.
First, the distribution of each severity level is uneven, with high and critical vulnerabilities comprising nearly 60% of vulnerabilities, which still leaves teams with quite a long list of security alerts to address. Also, while the CVSS rating attempts to reflect the characteristics and impact of a security vulnerability, it does not indicate risk, since risk is the impact times the likelihood.
#2 Application Type
Other times, teams prioritize mission critical apps or apps with sensitive data. However, those aren’t necessarily the most common attack targets. Another problem with relying on this method is that it’s difficult to build a methodology based on this parameter, since different organizations deal with different and subjective variables like user audience, mobile or web application, and more.
#3 Popularity
Some teams consider the popularity of a vulnerable component when deciding whether it requires immediate attention, figuring that they are the most attractive target for hackers. While popular open source vulnerabilities do in fact garner attention from the hacker community, there are additional parameters, and popularity isn’t the only determining factor when it comes to a vulnerability’s risk level.
#4 Disclosure Date
We found that a common practice for organizations that can’t handle a hefty backlog of alerts is to wipe the slate, creating an arbitrary cut-off point for older vulnerabilities. Unfortunately, according to Verizon’s Data Breach Investigations Report (DBIR): “Hackers use what works, and what works doesn’t seem to change all that often. Secondly, attackers automate certain weaponized vulnerabilities and spray and pray them across the internet, sometimes yielding incredible success.”
#5 Ease of Remediation
Another popular method is to prioritize the vulnerabilities that are easiest to fix. While this may help teams address a lot of issues in a small amount of time, it in no way guarantees that they are addressing the most urgent issues.
No Prioritization Method = Friction, Wasted Time, and Unnecessary Risk
Unfortunately, currently no golden standard exists for vulnerabilities prioritization. Each company, and sometimes even different teams within the same organization, prioritize in their own way. It should come as no surprise then, that our postA Rapidly Changing Digital World Drives AppSec Reinvention revealed that application security professionals rated vulnerability prioritization as their top challenge in implementing and running their AppSec programs.
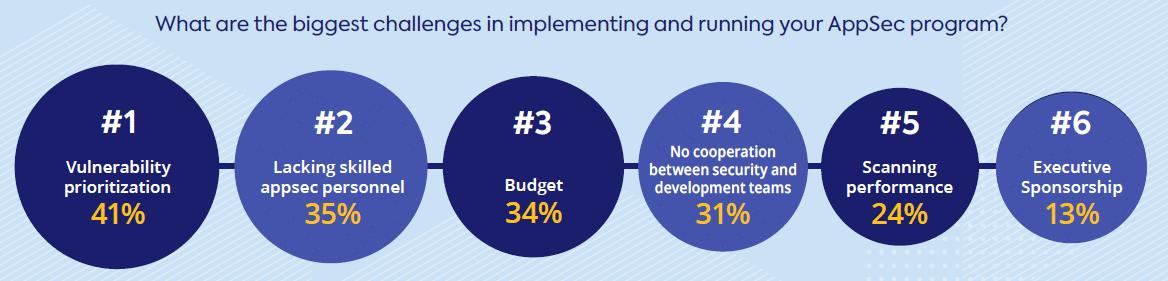
Prioritizing vulnerabilities has become an issue that often takes up a lot of development and security outfits’ time, due to the lack of a standard or agreed-upon best practice when it comes to determining which vulnerabilities must be fixed first. What’s the best way to prioritize is a conundrum that many development teams are still attempting to figure out.
Meanwhile, teams are making ad-hoc decisions or following separate guidelines and dealing with a lot of friction along the way. This inevitably leads to even more wasted time and runs the risk of letting the most critical vulnerabilities fall through the cracks.
Priority Scoring: Going One Step Further Than Detection
Organizations must find a way to prioritize their seemingly endless list of security alerts without slowing down the pace of development. The solution: vulnerability detection tools that come with prioritization technology built-in, saving the time and resources of reviewing individual vulnerabilities and debating what to fix first.
The next generation of vulnerability detection tools enables teams to go one step further with priority scoring. Priority scoring is an innovative approach that combines perceived risks from both security and non-security metrics. It factors in business impact as part of overall vulnerability scoring, ensuring the vulnerabilities that pose the biggest risk to your organization’s bottom line are addressed first.
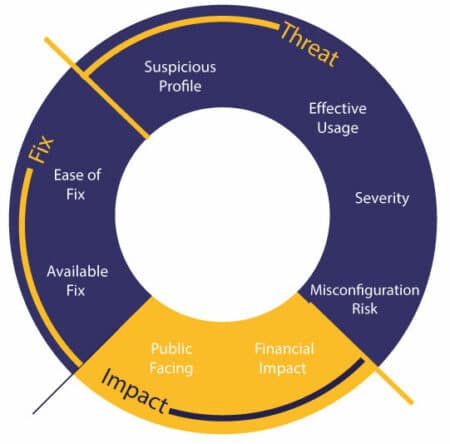
Priority scoring automatically remediates vulnerabilities using the following comprehensive business metrics:
- Threat – This factor assesses the vulnerability severity (CVSS score) and whether the vulnerability is called by proprietary code.
- Impact – The potential business impact of a vulnerability is evaluated, such as whether financial data or PII could be exposed.
- Fix – This metric determines whether a fix is available and how easy it is to remediate.
Getting Vulnerability Priority Scoring Right
The future of automatic vulnerability prioritization provides actionable insights and remediation advice. In a mountain of security alerts, priority scoring automatically detects the security vulnerabilities that most impact your business so that developers can address them first.
This innovative approach helps teams bring more agility to the prioritization process and helps them quickly locate and remediate the vulnerabilities that present the biggest security threat to their applications. No more wasted time, friction, or debates over which vulnerabilities come first. The new gen of detection tools gets prioritization right so that organizations can release secure products on time.
